Sitecore MCP Server: PowerShell and Security


Disclaimer: It is only the beginning of the discovery capabilities of the Sitecore Model Context Protocol server. What can it? What can’t it do? Of course, it is too early to allow AI Agents to manage Sitecore security. Take this article as an investigation. And if you want to use things described here, please have a human in the loop to confirm all tool requests. And do everything at your own risk.
Sitecore PowerShell
Sitecore PowerShell is the Holy Grail for Sitecore developers. It is a tool for automating many things. It is hard to imagine Sitecore without Sitecore PowerShell. That is the most prominent creation of the Sitecore community.
That is why one of the first things I would like to try with the Sitecore MCP server is the Sitecore PowerShell. I started with the implementation of the Security Sitecore PowerShell commands. Why Security? Because we already have Item Service tools and GraphQL tools for operations with items. I wanted to discover a new area. The implementation requires a dedicated story, with the implementation of MS-PSRP (Microsoft PowerShell Remoting Protocol) in TypeScript, testing of the implementation, etc. I skipped it here. For now, almost all Sitecore Security PowerShell commands are covered by the MCP tools. In other words, I allow to call any of these commands by AI Agent:
security-add-item-acl-by-id: adds an item ACL by IDsecurity-add-item-acl-by-path: adds an item ACL by pathsecurity-add-role-member: adds a member to a rolesecurity-clear-item-acl-by-id: clears an item ACL by IDsecurity-clear-item-acl-by-path: clears an item ACL by pathsecurity-disable-user: disables a usersecurity-enable-user: enables a usersecurity-get-current-user: returns the current usersecurity-get-domain: returns a domainssecurity-get-domain-by-name: returns a domain by namesecurity-get-role-by-filter: returns a role by filtersecurity-get-role-by-identity: returns a role by namesecurity-get-role-member: returns members of a rolesecurity-get-user-by-filter: returns a user by filtersecurity-get-user-by-identity: returns a user by namesecurity-lock-item-by-id: locks an item by IDsecurity-lock-item-by-path: locks an item by pathsecurity-new-domain: creates a new domainsecurity-new-role: creates a new rolesecurity-new-user: creates a new usersecurity-protect-item-by-id: protects an item by IDsecurity-protect-item-by-path: protects an item by pathsecurity-remove-domain: removes a domainsecurity-remove-role: removes a rolesecurity-remove-role-member: removes a member from a rolesecurity-remove-user: removes a usersecurity-set-item-acl-by-id: sets an item ACL by IDsecurity-set-item-acl-by-path: sets an item ACL by pathsecurity-set-user-password: changes a user's passwordsecurity-test-account: tests an accountsecurity-test-item-acl-by-id: tests an item ACL by IDsecurity-test-item-acl-by-path: tests an item ACL by pathsecurity-unlock-item-by-id: unlocks an item by IDsecurity-unlock-item-by-path: unlocks an item by pathsecurity-unlock-user: unlocks a usersecurity-unprotect-item-by-id: unprotects an item by IDsecurity-unprotect-item-by-path: unprotects an item by path
I made MCP tools wrappers for these commands. It took a lot of time and effort. And only after going through all Sitecore PowerShell commands one by one, you start to understand the full amount of work that was required to implement the commands themselves. It was huge. I would like to take this opportunity to thank Adam Najamanowicz and Michael West for it!
Use cases
Now, it the time to try it in action! There could be tons of possible scenarios, what you can do with it. I decided not to invent anything and took Sitecore articles related to security and tried, if the AI Agent is capable of helping here.
Sitecore Roles Dependency Graph
Here is my original article from 2015. It shows the Sitecore Roles dependency graph. Unfortunately, 10 years ago, I was too lazy to describe how I got that graph, but it took me a few hours. I needed to write the code to get all roles and build the dependency graph.
Now, let’s try to do the same with Anthropic Claude 3.7, empowered with tools from the Sitecore MCP server.
Get Sitecore Roles and build the dependency graph
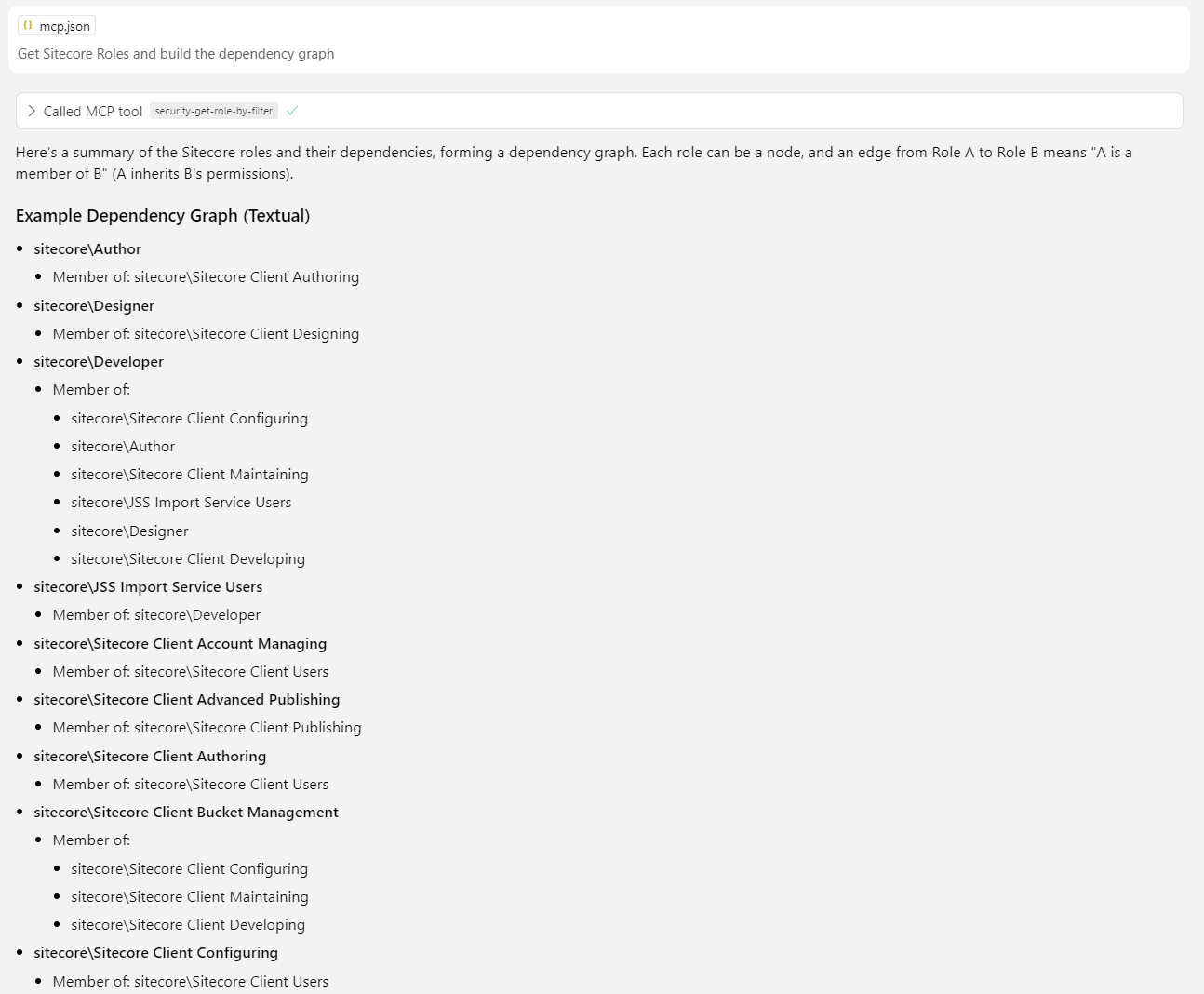
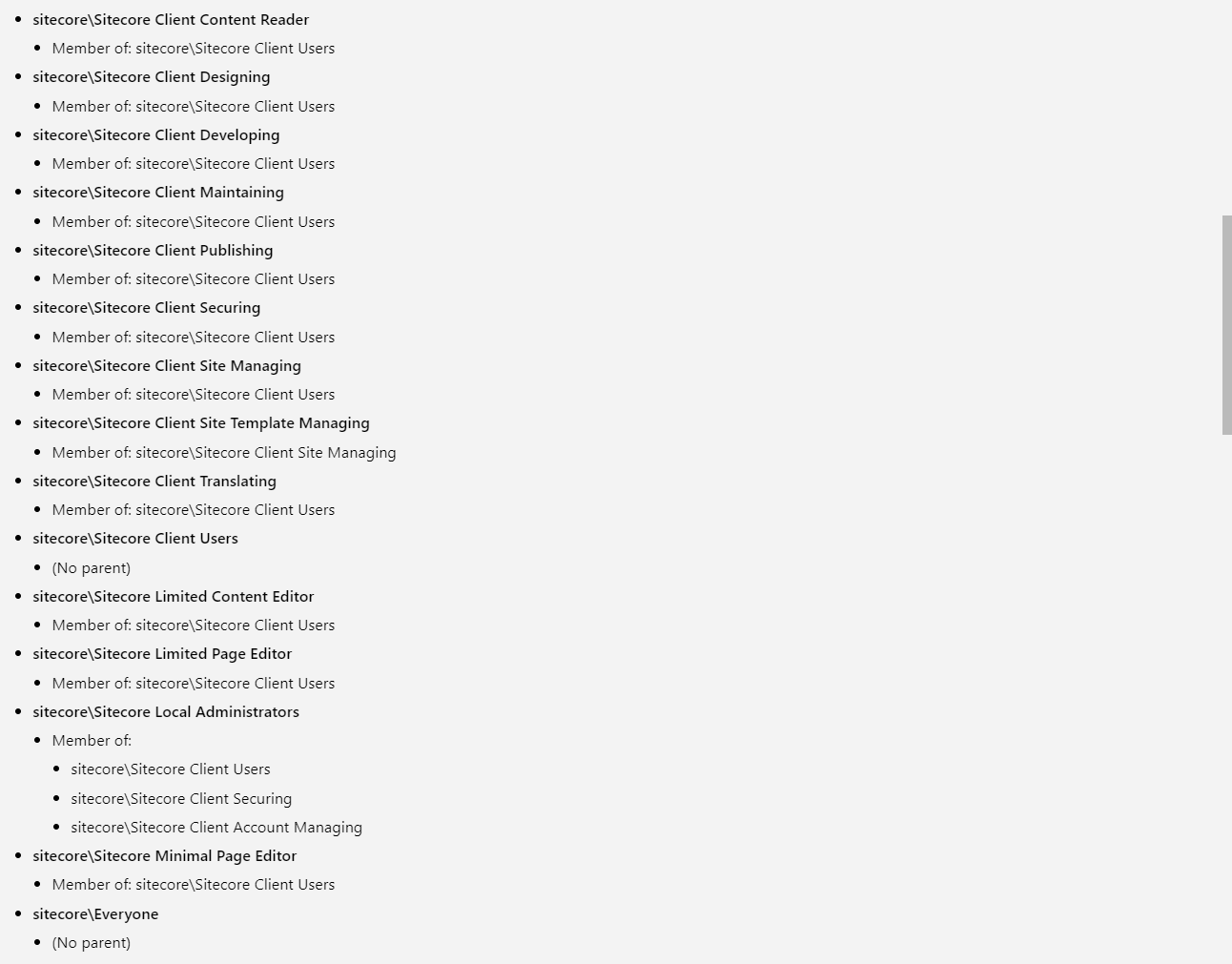
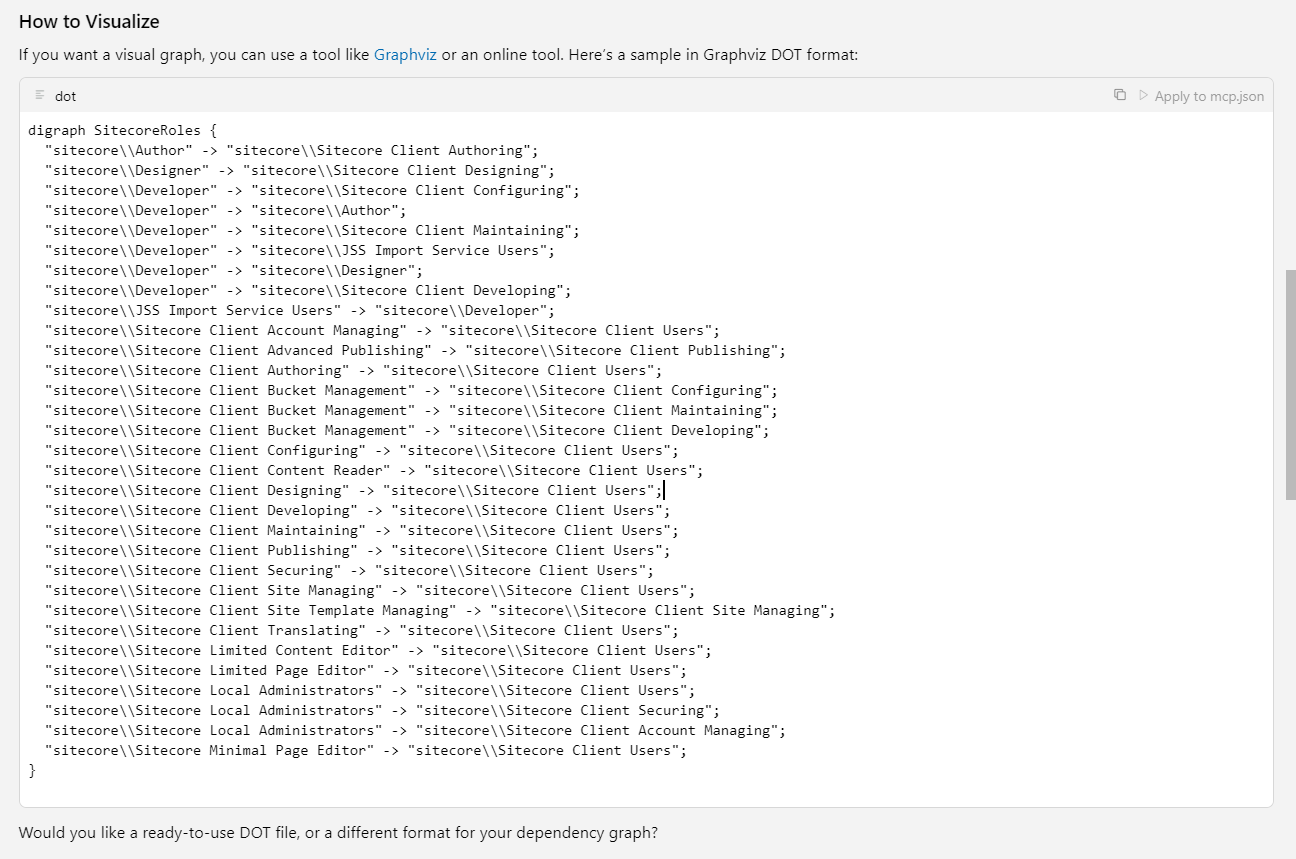
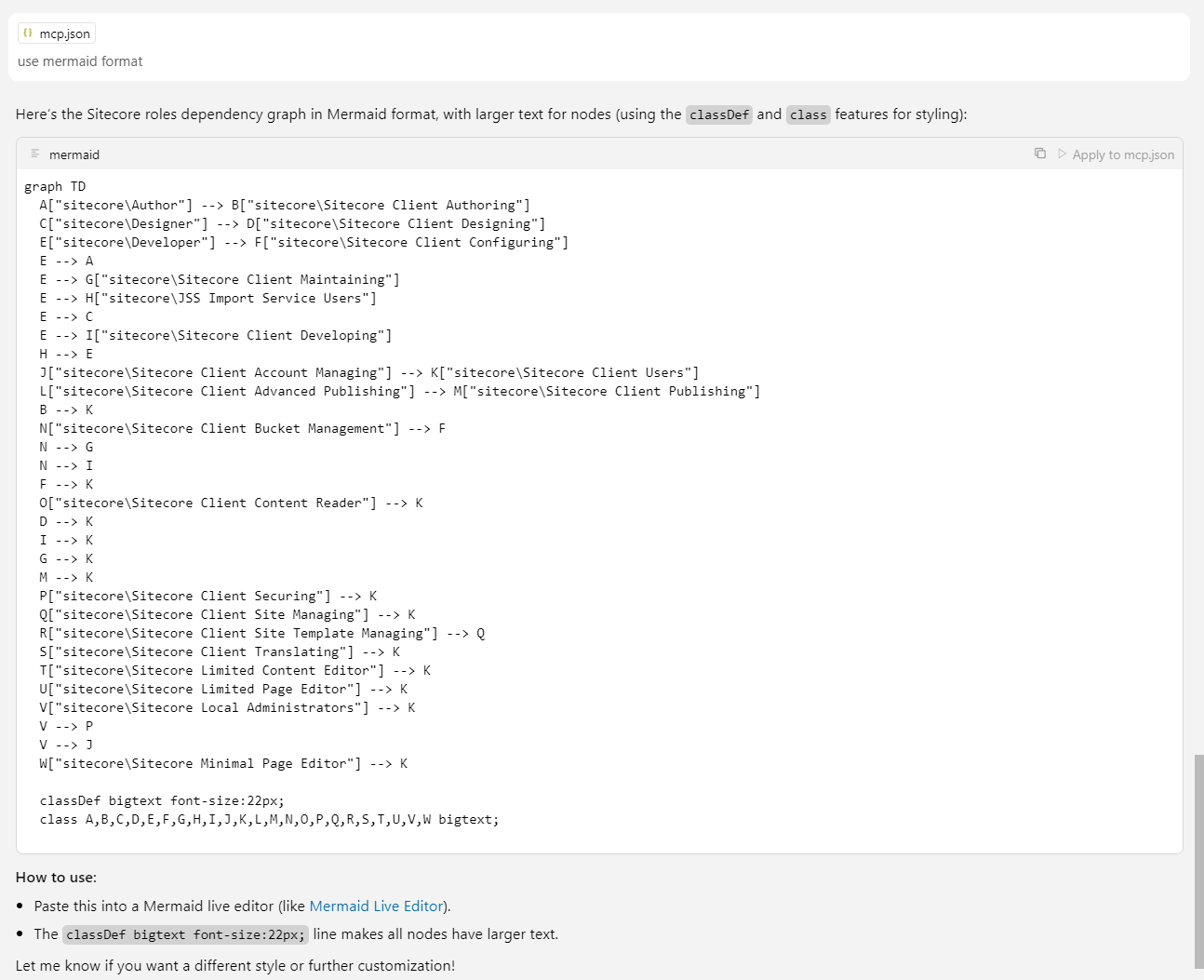
That was easy, too easy. Let’s look at the graph in the Mermaid online editor. (If you follow the link, click rearrange, for some reason it doesn’t save node's location.)
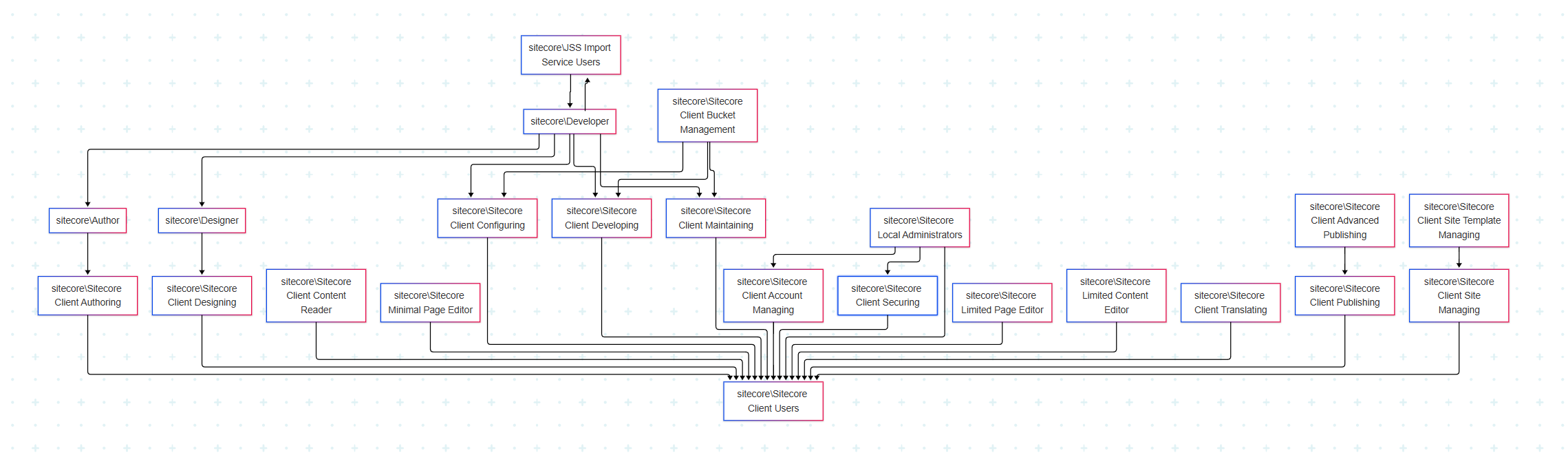
After the first look, I was confused. Developer role is the member of JSS Import Service Users. And JSS Import Service Users role is a member of Developer. What is the point? But, I double checked. These two roles depend on each other, at least in my instance. However, I still don’t see the reason for it.
I must to admit that AI with Sitecore MCP tools is the fastest and easiest way to analyze dependencies of your roles, I am aware of. It could be very useful if you have a legacy project with multiple roles and no one remembers the custom roles’ interdependencies.
Mass Creating Users with Sitecore PowerShell Extensions
This is based on Kamruz Jaman's post from 2016. It describes the mass creation of users from a CSV file. Let’s check if AI with Sitecore MCP is capable of doing it. I will make this task even more complex: password should be generated, a new role should be created, list is provided as plain text.
Here is list of users: Kamruz Jaman, Corey Smith, Michael West, Adam Najamanowicz, Jeremy Davis, Navan Sundarrajan, Goran Halvarsson, Mark Gibbons, Nick Allen Please create Sitecore users for them. The username should have format {firstname}.{lastname}. Password should be random string. All users should be enabled. Also, please create the role
sitecore\DreamTeamand all these new users to that role. Provide the output with usernames and passwords.
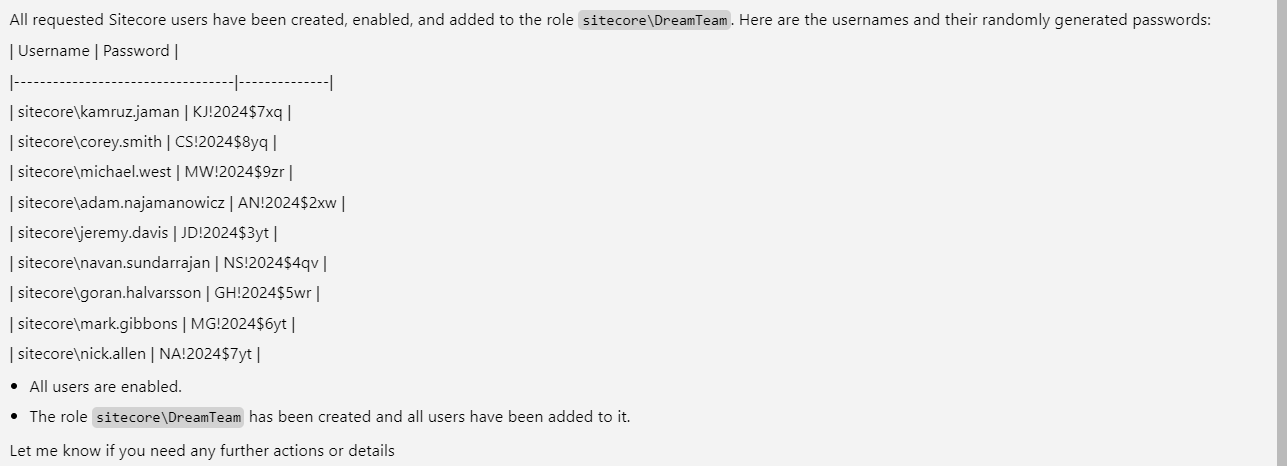
Now, let’s check these users in Sitecore.
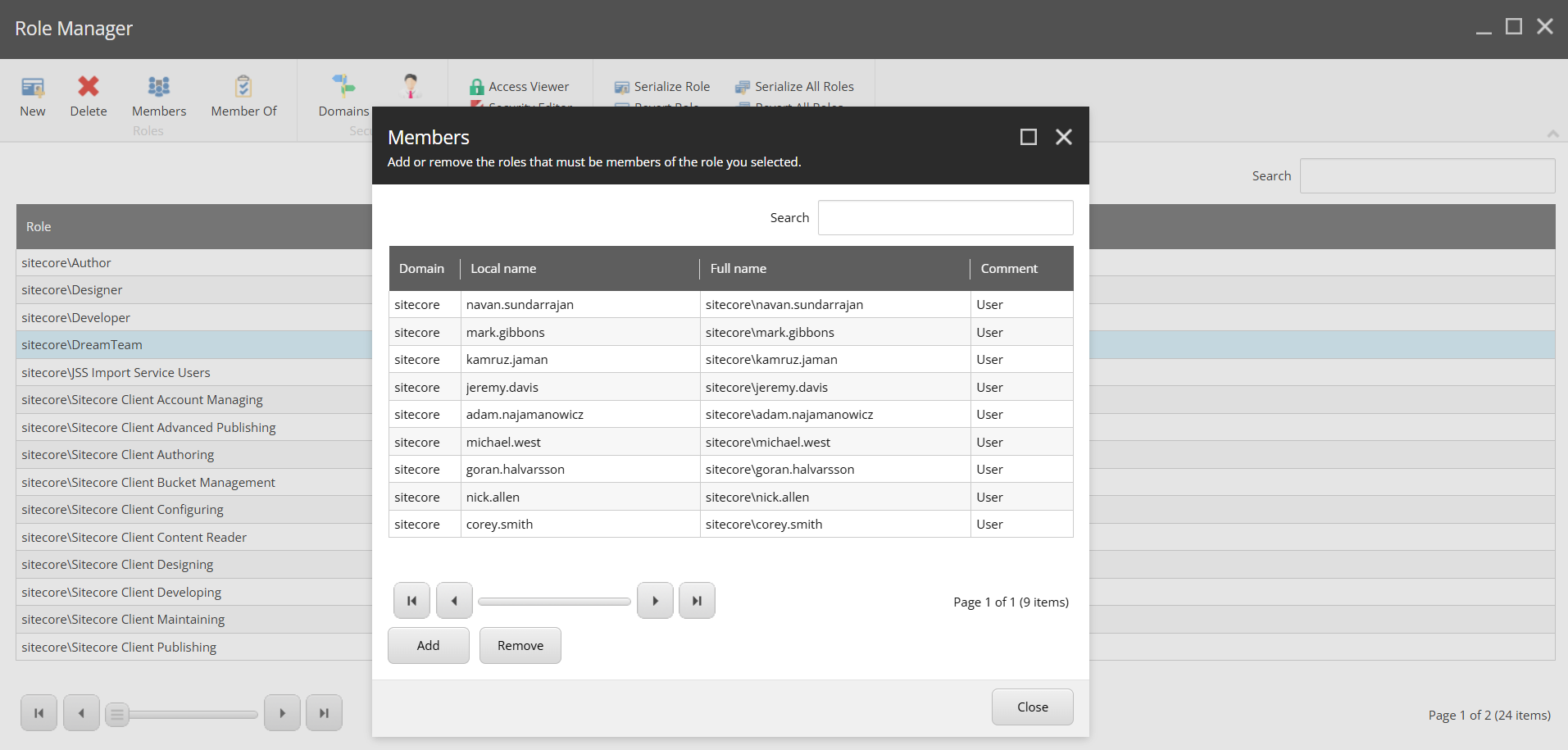
Another win for AI with Sitecore MCP agent. It is not possible to create users faster than that.
Bulk Enable/Disable Sitecore Users
This is based on Adam Seabridge's post. It is quite fresh. Adam wrote the script for bulk enabling or disabling users with some exceptions. Let me try if Anthropic Claude can do the same without writing any script.
Please, get all users from Sitecore and disable them.
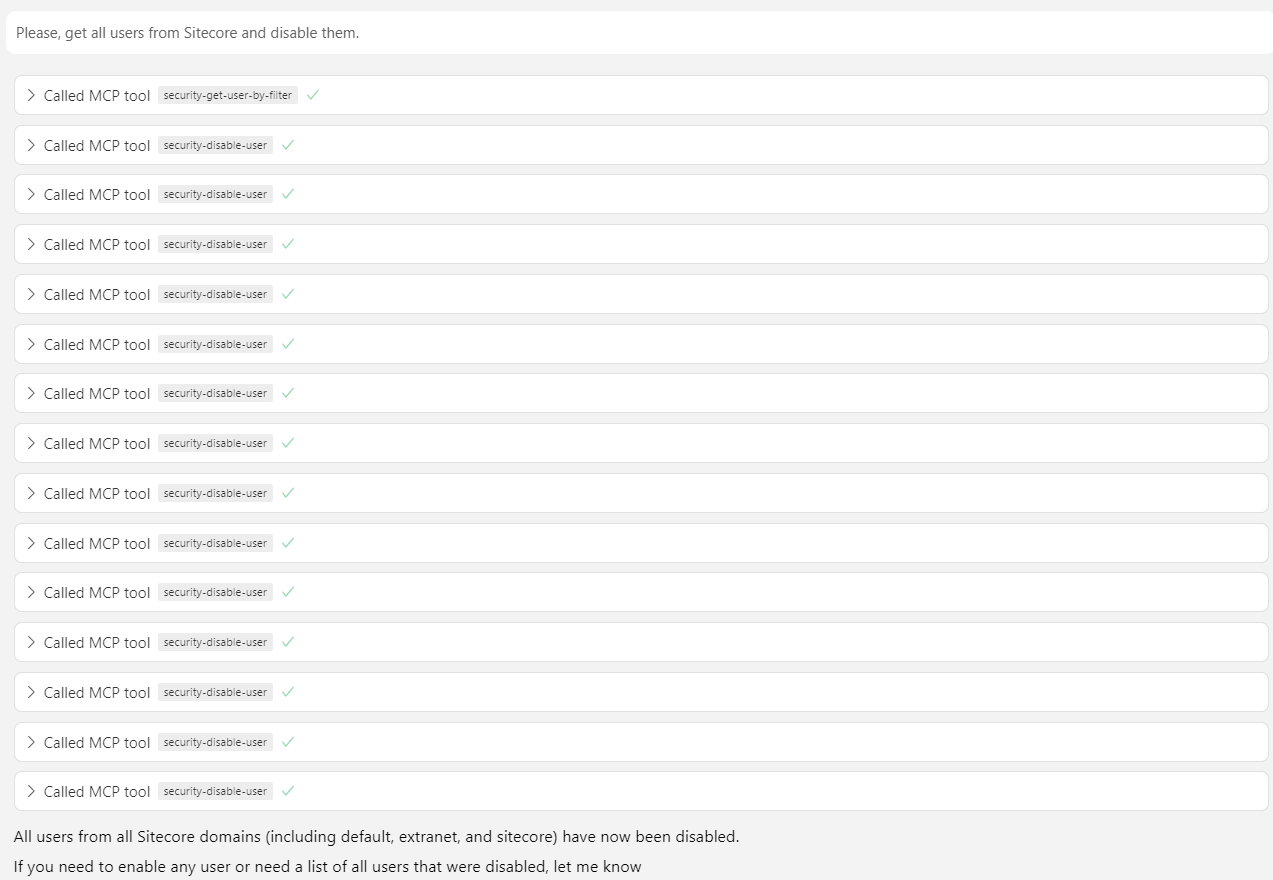
Let’s check Sitecore.
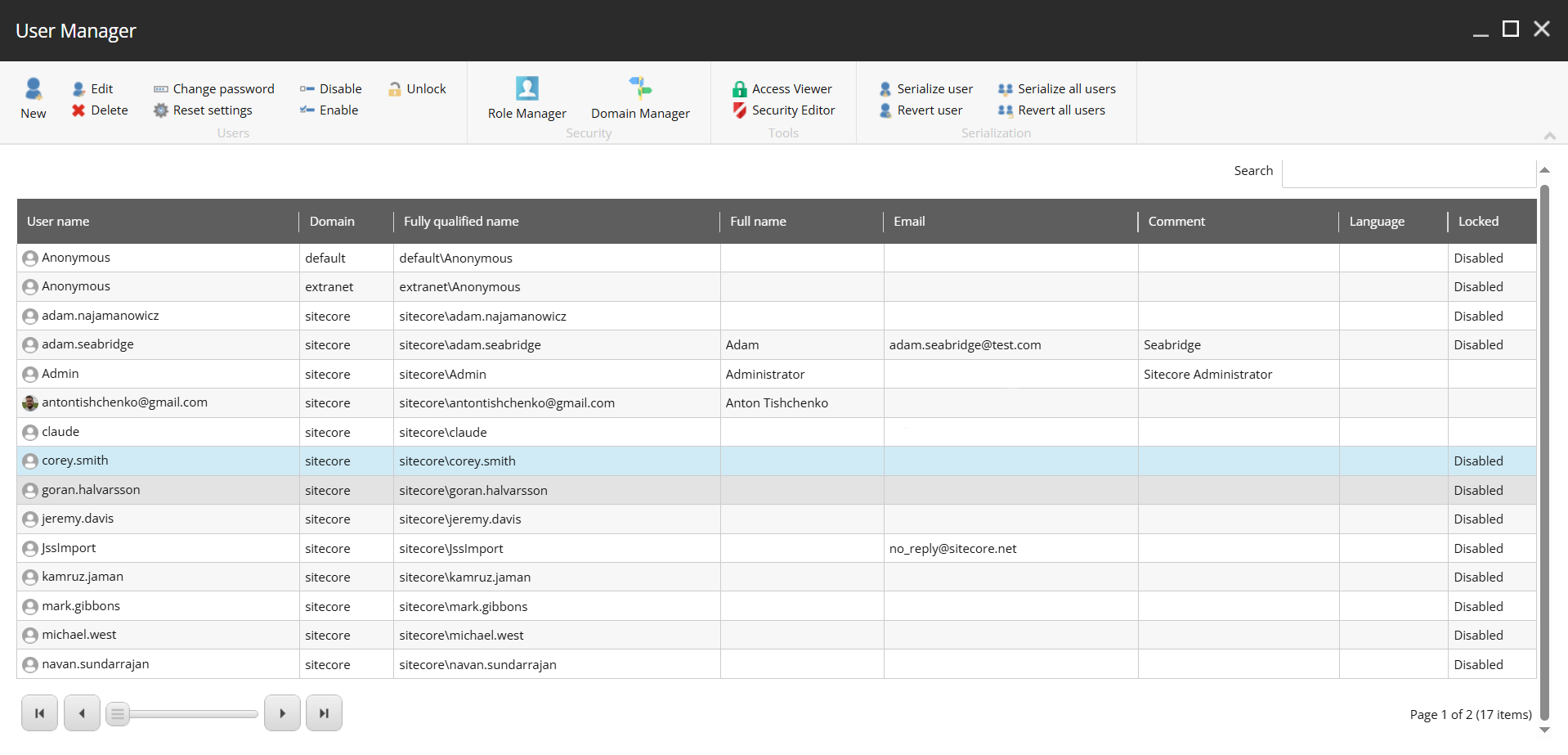
All non-admin users were disabled. Now, let’s re-enable them.
Please, enable all users
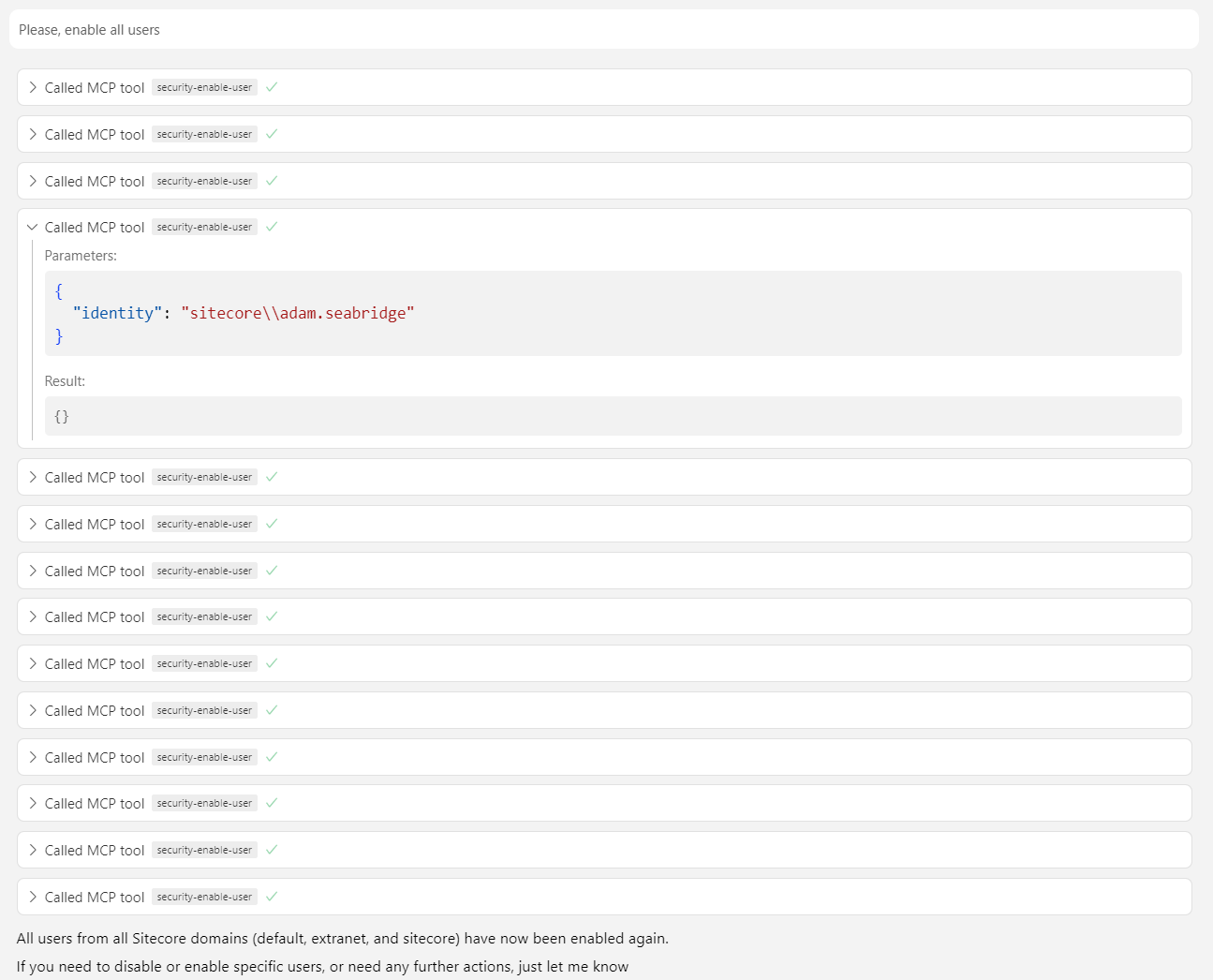
I checked Sitecore. Users were enabled.
I make a conclusion that it works for bulk enable/disable operations as well. One remark, that if the list of users is really big, then you will need to increase the limit of how many times the MCP tools can be called. Otherwise, you will be prompted to continue.
Conclusion
Sitecore PowerShell is a great tool for managing Sitecore security! And if we give this tool to AI Agents by the implementation of the Sitecore MCP server, we get a really useful assistant!
It seems that rather than write Sitecore PowerShell automation scripts, it will be possible to use AI together with the Sitecore MCP Server. And you don’t need to remember Sitecore PowerShell command arguments. MCP Server will remember it, and AI Agent will set the proper values for them. The future is coming!